Cloud security posture management (CSPM) is a rapidly growing sector essential for modern organizations leveraging the cloud. With threats becoming more sophisticated and cloud environments more complex, CSPM solutions have become key to maintaining robust security, ensuring compliance, and harnessing the benefits of automation and artificial intelligence.
Introduction to Cloud Security Posture Management
Cloud security posture management is a comprehensive approach to safeguarding cloud infrastructure by continuously monitoring configurations, identifying risks, and automating remediation. As enterprises migrate core workloads to the cloud, misconfigurations, compliance issues, and lack of visibility become growing threats. CSPM tools are designed to tackle these risks across public, private, and hybrid cloud environments.
Industry Statistics and Market Growth
- The CSPM market is valued at over $6.43 billion in 2025 and is set to reach $15.6 billion by 2033, growing at a CAGR of 10.37%.
- Only about 26% of organizations have implemented CSPM, despite 87% adopting multi-cloud strategies and 72% utilizing hybrid cloud setups.
- 80% of companies reported serious cloud security issues in 2023; over 60% had public cloud-related incidents in 2024.
- 45% of data breaches now occur in the cloud. The average cost of a breach is $4.35 million.
- 91% of organizations identify AI as a priority for future security strategies; AI-enhanced CSPM tools are continuously improving threat detection and accountability.
- 56% of organizations struggle to secure data across multi-cloud environments, highlighting the need for automated solutions.

Major Challenges Facing Organizations
- Organizations adopting or expanding their cloud presence face several challenges:
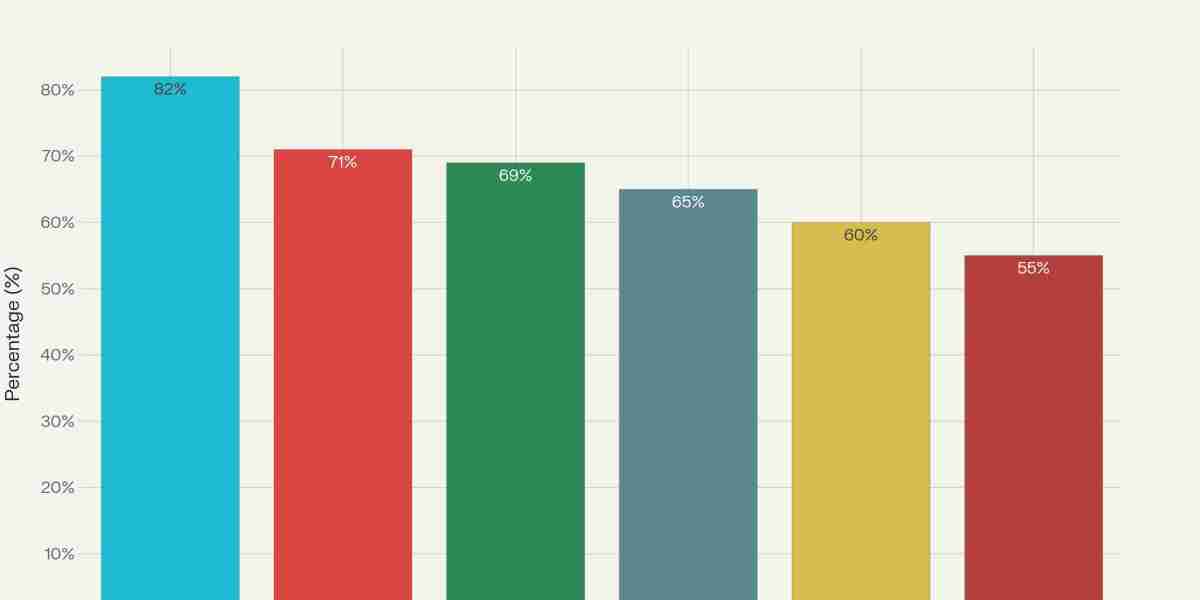
- Cloud misconfigurations account for 23% of incidents; 82% are due to human error.
- Multi-cloud strategies increase complexity; 69% of companies report difficulties maintaining consistent controls across platforms.
- Skills shortage: 71% report a lack of skilled cloud security professionals.
- Alert fatigue and false positives: High alert volumes overwhelm security teams; prioritization and validation are top needs.
- Unclear shared responsibility: Many organizations misunderstand which aspects of security are their responsibility versus the cloud provider’s, leading to gaps.
- Compliance and visibility: Maintaining compliance with frameworks like CIS, NIST, PCI, and HIPAA across dynamic cloud resources is a continuing struggle.

How CSPM Products Help
- CSPM solutions are designed for these dynamic, large-scale environments, providing:
- Continuous assessment and real-time risk analysis using AI and automation for threat detection and guided remediation.
- Monitoring and visibility across assets and configurations, supporting compliance with security standards.
- Auto-remediation and policy enforcement that adapts as infrastructure changes, preventing misconfigurations from leading to breaches.
- Integration with existing workflows and security information/event management (SIEM) platforms, automating ticketing for issues and aligning with SOC operations.
- Support for natural language queries and AI-driven analytics, allowing broader access and faster insights across teams.
- Scalability to manage posture across hybrid and multi-cloud deployments, helping organizations maintain security consistency.

FAQ Most Searched
1. What is cloud security posture management (CSPM)?
CSPM comprises automated tools and processes designed to continuously monitor, assess, and improve the security posture of cloud infrastructure by identifying, alerting, and remediating misconfigurations and policy violations.
2. Why do organizations need CSPM?
Organizations require CSPM to reduce cloud risks, prevent costly security breaches, manage compliance obligations, and gain unified visibility into complex, fast-changing cloud environments.
3. How does CSPM differ from traditional cloud security?
CSPM focuses on configuration, visibility, and compliance in cloud-native environments, often using AI and automation, while legacy security tools center on endpoint and perimetric defense, which are less effective for dynamic cloud resources.
4. What are the benefits of AI in cloud security posture management?
AI in CSPM enhances real-time threat detection, prioritizes alerts based on risk, automates remediation, and continually learns from the evolving threat landscape for smarter protection.
5. How can CSPM help with multi-cloud security?
CSPM tools unify risk management, compliance, and monitoring across all cloud providers, giving organizations a single dashboard for multi-cloud environments and helping maintain consistent policy enforcement.
6. What are the most common cloud security misconfigurations?
Typical misconfigurations include open storage buckets, excessive permissions, unencrypted databases, poorly secured APIs, and lack of network segmentation-all of which CSPM tools can automatically detect.
7. How does CSPM assist with compliance requirements?
CSPM solutions benchmark cloud resources against standards such as CIS, NIST, PCI, and HIPAA, continuously auditing configurations and generating reports for regulatory compliance.
8. What is the financial impact of poor cloud security posture?
A single cloud data breach can cost an average of $4.35 million, not including regulatory fines and reputational damage, making robust CSPM critical for risk mitigation.
9. How can CSPM reduce alert fatigue for security teams?
Modern CSPM platforms use AI to filter, group, and prioritize alerts based on severity and context, reducing the noise and enabling teams to focus on critical risks.
10. What are the core features to look for in a CSPM solution?
Essential features include continuous asset discovery, risk assessment dashboards, policy enforcement, compliance management, automated remediation, real-time reporting, and multi-cloud support.
11. How does CSPM integrate with existing security operations?
Most CSPM solutions easily integrate with SIEM, SOAR, ITSM, and DevOps pipelines, allowing security teams to automate workflows and incident responses.
12. What industries benefit most from cloud security posture management?
Industries handling regulated, sensitive, or mission-critical data-such as finance, healthcare, government, technology, and retail-see the greatest value from CSPM adoption.
13. What role do GenAI and machine learning play in CSPM?
GenAI and ML power smarter detection, classify assets and threats, recommend remediations, and even automate risk scoring and tagging for better cloud governance.
14. How do CSPM tools handle false positives and prioritize alerts?
AI-driven CSPM tools contextualize events, correlate findings, and assign risk levels, which helps security analysts focus on issues most likely to impact the organization.
15. What’s the difference between CSPM and CNAPP?
CSPM secures the configuration and compliance posture; CNAPP (Cloud-Native Application Protection Platform) integrates CSPM with workload protection, DevSecOps, and runtime threat detection for end-to-end cloud security.
16. How does CSPM improve cloud visibility and asset management?
CSPM automatically discovers cloud assets across environments, mapping configurations, permissions, and changes, thereby giving organizations a real-time inventory and status report.
17. Can CSPM automate remediation of misconfigurations?
Yes, advanced CSPM tools can automatically fix detected misconfigurations or unsafe policies based on predefined rules, reducing manual effort and response times.
18. Is cloud security posture management necessary for small businesses?
Absolutely-small businesses face the same risks as enterprises, and as they increasingly adopt cloud services, CSPM helps protect them from breaches and compliance failures.
19. What are the challenges of implementing CSPM?
Challenges include integrating with complex multi-cloud setups, managing false positives, user training, setting up correct governance, and customizing compliance frameworks.
20. How are regulatory changes influencing CSPM adoption?
New regulations around data privacy, cybersecurity, and sector compliance are making CSPM essential, as these solutions can automate policy enforcement and evidence collection.
Conclusion
With cloud adoption surging and threat actors increasingly targeting cloud infrastructure, CSPM has become indispensable for organizations of all sizes. Automation, AI, and integration capabilities make these tools critical for defending dynamic environments, preventing costly breaches, and staying compliant with a complex patchwork of regulations. Advanced solutions like those from CoreStack and similar leaders bring together the best of technology and best practices, helping organizations secure the cloud era
Originally published at https://corestackio.blogspot.com on October 16, 2025.